Cyber threat intelligence is information useful for an organization through which they plan to protect themselves from threats. This information is useful to know, prevent, and identify Cyber threats that are potential and may damage valuable resources.
Cybersecurity has the power to predict future threats even before they attack and reach the target to make potential damage. Moreover, it helps organizations to speed up their response time & decision-making process, better security to the organizational data, etc. For this reason, Cyber threat intelligence was introduced.
Cyber threat intelligence is the change of security approach from reactive to proactive intelligently. It helps to get knowledge on current threats, attack vectors, existing issues, threat attackers that are specific to your industry, etc. Moreover, we can analyze and compare them to find the best way with intelligence that helps us prevent cyber attacks on our infrastructure.
Let us discuss further in detail about Cyber threat intelligence and its various aspects.
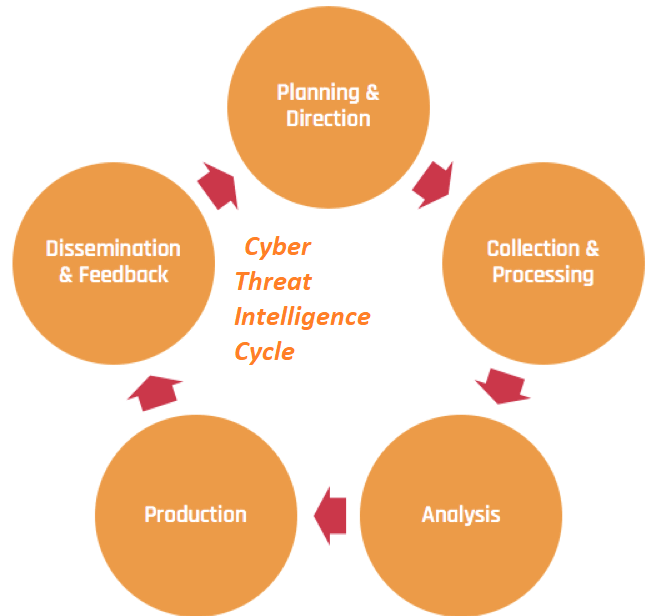
Cyber threat intelligence cycle
It is necessary for any Org. to define the goals for the Cyber threat intelligence lifecycle to make a protection plan. However, it may vary from one another. The traditional intelligence mainly focuses on six different stages of Cyber threats. This is what we call the Cyber threat intelligence lifecycle. Moreover, we will discuss them in detail below:
Direction
The direction phase is the first stage of the lifecycle where we set up goals for the Cyber threat intelligence program. Moreover, it involves understanding and formulation of various things. Such as:
- The valuable data/assets and business processes that need protection.
- The potential changes in losing those assets or disturbing those processes
- The types of CTI that the security team within the Org. requires to protect assets and respond to threats.
- Planning about what to protect and prevent attacks.
Once the intelligence and protection needs are determined, the business entity can formulate a channel to opt for those needs for various requirements.
Get updated skill on threat intelligence with ITGuru by stepping into the Cyber Security Online Course.
Collection
Now it comes to the collection stage. It is the process of collecting information to focus on the most important intelligence needs for the organization. Data or information gathering includes various organic & variety of sources. This includes:
- Pulling out metadata and log information from internal networks and security sources
- Getting threat data feeds from industry organizations and various cyber security vendors
- Holding several talks and intelligent interviews with well-informed sources
- Scanning open-source news and blogs through various channels
- Gathering and removing various websites and forums to check Cyber threat trends
- Getting access to the closed sources
Moreover, the data collected will include processed information like intelligence reports, raw data, etc. So, that’s the collection phase.
Processing
The processing stage is the transformation phase of the collected information into a useful means by the business entity. Moreover, all the raw data collected should be processed, either by human beings or intelligent systems. Various collection methods require various types of processing systems.
We can use another example such as; extraction of IP addresses from a security vendor’s report. And can add them to a CSV file for importing a product. In a more technical context, processing may include the collection or extraction of indicators from an email. Moreover, filling it with other rich information, and then sharing the same with the end-user protection tools to automate blocking.
Analysis
This is generally a human process. It converts the processed information into intelligence reports to inform important decisions. These decisions include whether to detect & investigate a potential threat, actions to be taken immediately to prevent a threat, etc. Moreover, it also involves strengthening security controls, the investment required in additional security resources, etc.
The delivery of intelligence reports may include different types of audiences. Say, a video file, PowerPoint presentation, etc. A successful Cyber threat intelligence team provides regular technical reporting to other security intelligence teams with external context. This will be regarding malware, virus attackers, and the latest cyber threat trends.
Dissemination
The dissemination is a process that involves getting the completed intelligence report result to the places it needs to go. Most cybersecurity entities have different teams that get benefit from cyber threat intelligence.
There are many audiences, whom we need to ask the following to get information:
- What type of Cyber threat intelligence do they need, and how the external data support their various activities?
- In what manner should we provide updates and other data?
- Moreover, through which media should the intelligence process be spread?
- How should we follow up or contact if they have any queries?
The above information needs to collect from the different people or clients to provide the best cyber threat intelligence protection plan.
Feedback
It is one of the important parts of the Cyber threat intelligence to get feedback from people. It is very important to understand the whole intelligence priorities of the org. And it also needs to know the requirements of the security teams that consume the cyber threat intelligence. Moreover, their needs show the way to all stages of the intelligence lifecycle and let us know about:
- What kind of data to be collected?
- How to process and modify the data to make it useful information?
- How to analyze the data and visualize it as an intelligence action?
- To whom each type of intelligence should be widespread?
- How actively it needs to be widespread, and how fast to respond to queries that come in?
All the above things need to be prioritized and get proper feedback on all. In this way, the lifecycle of cyber threat intelligence comes to an end. The whole cycle makes the sense of using threat intelligence perfectly to get maximum results.
Types of threat intelligence
There are three different types of threat intelligence in Cyber threat intelligence.
- Strategic
- Tactical
- Operational
Each of these types serves different purposes in collecting and visualizing data and its execution.
Let us get into the details of the three threat intelligence types.
Strategic threat intelligence
The strategic threat intelligence conducts high-level analysis for long-term issues intended for non-technical audiences. Such as; board members, stakeholders, business promoters, etc. This type of intelligence help in making several informed decisions and also produces the capabilities of the cyber threat.
Moreover, the strategic threat intelligence aims at understanding the wide trends affecting the cyber platform. This kind of Cyber threat intelligence sources may be different from the usual one. It includes news and media (local & national), reports, online activities, etc.
Tactical threat intelligence
The tactical intelligence under CTI aims to help teams in daily operations like working with IOCs. It helps to locate those existing security systems whether to work successfully in identifying and reducing risk. The intelligence system locates the IOCs or indicators of compromise. Moreover, it also enables the responders to locate and eliminate any network issues. Further, this is useful to inform the changes and improvements to the existing security controls.
Examples of this kind of intelligence are unusual traffic, an increase in download requests, etc. Thus, it is treated as the most basic type of intelligence that usually automates being simple intelligence to produce. Besides, this type of intelligence has a short life span. It makes the technical audience think over the cyber threats that may occur in a lifetime.
Operational threat intelligence
This type of intelligence helps businesses by answering queries like who? how? etc. This is achieved by gathering past data about any known threats/attacks located by the tactical system. Moreover, it helps the security teams by providing the necessary factors like intention, timing, and complexity of cyber-attacks. On this basis, they can understand the specific threats surrounding them. By knowing the insights, the security teams can react to the cyber-threats and help the organization.
Cyber threat intelligence management tools
Some tools within Cyber threat intelligence help in identifying potential threats and mitigate them. Here, we will discuss a few of these tools.
Automatic detection
There is a lot of data produced every day and to manually detect the threats inside data is not that easy. So, an automated detecting tool helps in this regard very much. The tool helps in locating the potential threats and clears them. As a result, it saves time and avoids manual testing hurdles. Moreover, it makes the teams shift data seamlessly. By automating processes, human errors will get reduce and the Cyber threat intelligence system will improve.
Consolidated management
It is difficult for every Org. to build effective communication lines across the unit. By making data consolidation, any enterprise can make it easy for the rest of the Org. for smooth operations. Hence, the team can focus on its core practices and makes the goals possible to achieve.
Moreover, the Org’s can do network traffic analysis, applying free research tools, the latest cyber security platforms, and updates. To reduce the risks of threats, a business can plan well by investing in these tools & platforms.
||{"title":"Master in Cyber Security", "subTitle":"Cyber Security Certification Training by ITGURU's", "btnTitle":"View Details","url":"https://onlineitguru.com/cyber-security-training.html","boxType":"reg"}||
Cyber threat intelligence use cases
There are many examples or use cases of threat intelligence that makes it a dynamic resource across organization and teams. Here are a few of the threat intelligence use cases to discuss.
Security Operations
The team of security operations regularly deals with a huge amount of alerts/alarms from the network they observe. Locating them and making inquiries is complex for these teams. Hence, cyber threat intelligence can help in solving these problems. It helps in identifying and collecting all threats faster and accurately, filters the false one, and speeds up the inquiry by simplifying incident analysis. Thus, it makes the security analysts free from wasting time on unwanted security alerts.
Risk Analysis
Risk analysis is a common way for business units to prioritize their investments. But most of these analyses are not quantified and with partial information of assumptions made, it becomes difficult to take action. Besides, this type of intelligence provides an accurate context for the risk models with defined risk measures and transparent data. This makes the business unit to make their investment the best one.
It also answers various queries that occur in the mind of a security analyst, Such as;
Which type of threats or attackers uses a specific type of attack & they target the industry?
How to identify them?
Has any other industry observed this type of threat in past?
How much vulnerable it would be?
There are many more queries like this may appear in front of the analysts. For all these Qs, this intelligence system only can provide solutions.
Fraud prevention
To keep the business unit safe, it’s not only enough to detect the threats and making solutions to prevent them. The analysts need to prevent fraudulent use of sensitive business data and its goodwill. Threat intelligence gathers all the information regarding fraudulent means or fraudsters. And it keeps motivating teams by presenting methods & tactics they use. The major types of frauds include;
Payment fraud:
Many attackers will be in thought to locate the potential people and their data to attract them for transacting. Using Cyber threat intelligence, we can observe the criminal communities, forums, fake websites, financial references, etc. to prevent the business from any major payment threat.
Data Compromising:
Cyber attackers or criminals regularly upload huge amounts of fake data like usernames & password credentials. Later, they make them available for sale on the dark web or fraudulent sites seem to be genuine. Hence, CTI helps to locate leakages in sensitive data, credentials, passcodes, financial data, etc.
Importance of Cyber threat intelligence
The main objective of cyber threat intelligence is to provide Org's a better understanding of the happenings outside their network. Moreover, it requires giving them the best idea of the cyber threats that brings the most risk to their infrastructure. The companies need this type of intelligence for effective defense of their selves.
Cost efficiency
The earlier report shows that a data breach costs US companies an average of $7 million. And the speed of detecting and responding to a breach makes an impact on that figure. There is no hidden surprise that effective threat intelligence can help clients. Moreover, if they are no complete avoid then at least cut down on the cost may take place.
Efficient Security team
When an unknown error within the network is detected, firm security staff alerts and they need to know its actual status. Whether the threat is real or merely a false positive, have to know. Mixing up this type of intelligence will give the business teams more insight into what needs to be found. Moreover, they can also improve their response rate towards queries. This makes the team more efficient to work.
Collaborative knowledge
Knowledge is the thing that grows rapidly in sharing. The same thing comes true with threat intelligence also. Moreover, the collaborative knowledge of the efficient Cyber threat intelligence teams makes the security department stronger.
Conclusion
Thus, it’s all about Cyber threat intelligence. Every business entity needs to protect its valuable assets from external threats or exploits. Moreover, the security team should be alert and make detections from all around the networks and systems. This makes them stronger and motivated to find out new trends in cybersecurity.
Get more practical knowledge of threat intelligence and their protection measures from the best. Join the Cyber Security Online Training from ITGuru. This learning may help you to gain professional knowledge of cybersecurity. This knowledge will also help you to get into a better place of work.